Secure Document Sharing: Protecting Your Confidential Information
In today’s digital world, sharing confidential documents safely is more critical than ever. Whether you’re handling legal contracts, financial reports, medical records, or proprietary business information, proper security measures can mean the difference between successful collaboration and devastating data breaches.
Understanding Document Sensitivity Levels
Highly Confidential Documents
- Legal contracts and agreements
- Financial statements and tax documents
- Medical records and patient information
- Intellectual property and trade secrets
- Personal identification documents
Business Sensitive Documents
- Internal reports and presentations
- Employee information and HR documents
- Strategic plans and roadmaps
- Customer data and contact lists
- Vendor agreements and proposals
Limited Distribution Documents
- Marketing materials and press releases
- Training materials and handbooks
- Policy documents and procedures
- Meeting minutes and agendas
- Project documentation
Essential Security Features for Confidential Sharing
Access Control Mechanisms
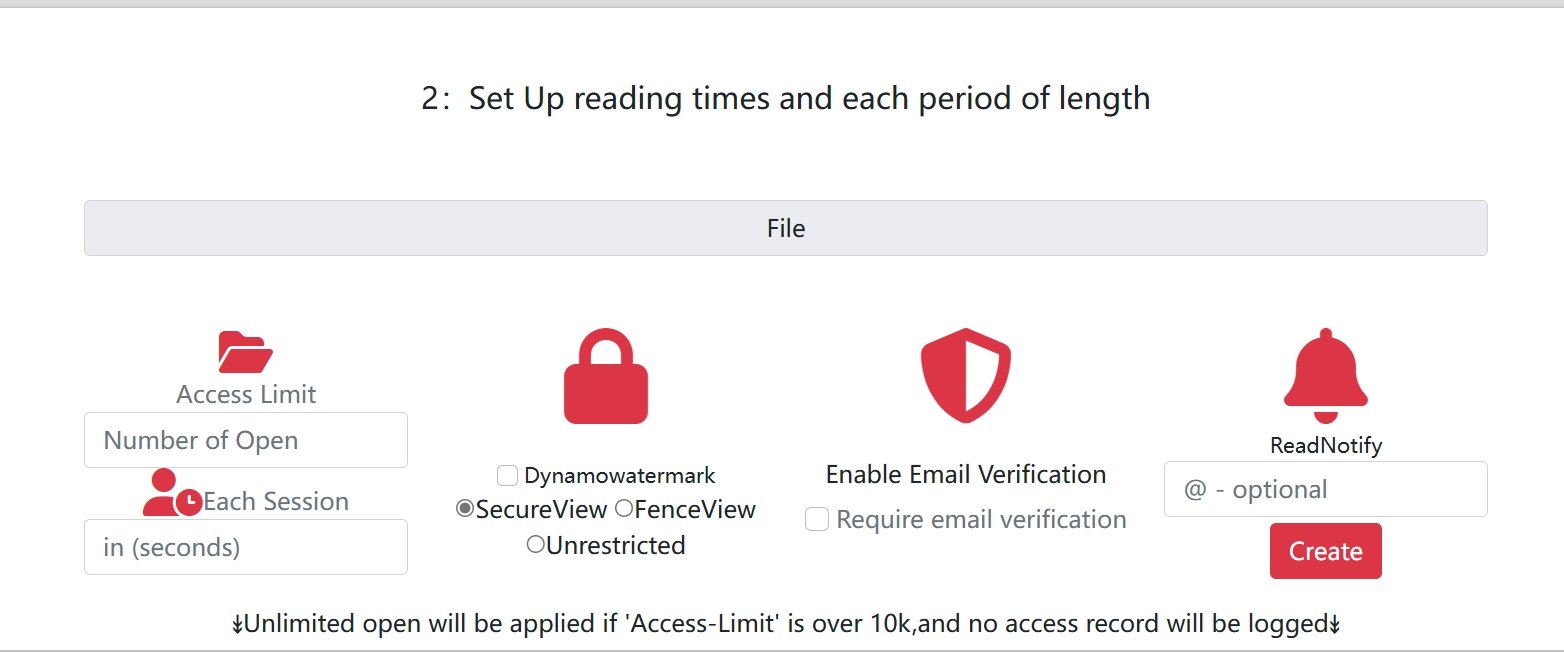
- View Limits: Restrict how many times a document can be opened
- Time-based Expiration: Set automatic expiration dates for document access
- Email Verification: Require email confirmation before viewing
- IP Restrictions: Limit access to specific geographic locations or networks
Content Protection Features
- Watermarking: Add visible or invisible watermarks to prevent unauthorized use
- Print Prevention: Disable printing capabilities to prevent physical copies
- Download Restrictions: Prevent users from saving local copies
- Screenshot Protection: Block screen capture attempts where technically possible
Step-by-Step Secure Sharing Process
1. Document Preparation
- Review document content for sensitivity level
- Remove any unnecessary sensitive information
- Ensure document is in final, approved format
- Consider adding internal watermarks or headers
2. Security Configuration
Security Settings Checklist:
□ Set appropriate access limits (1-50 views)
□ Configure expiration date
□ Enable email verification if needed
□ Add custom watermark text
□ Disable print/download if necessary
□ Set geographic restrictions if applicable
3. Recipient Management
- Verify recipient email addresses are correct
- Consider using individual links for each recipient
- Provide clear instructions for document access
- Set expectations for document handling
4. Link Distribution
- Use secure communication channels
- Avoid sending links through unsecured email if possible
- Consider using QR codes for in-person sharing
- Monitor access patterns through analytics
Industry-Specific Security Guidelines
Legal Profession
- Always use attorney-client privilege watermarks
- Set strict view limits (1-3 views typically)
- Enable email verification for all recipients
- Use expiration dates aligned with case timelines
- Maintain detailed access logs for compliance
Healthcare Organizations
- Implement HIPAA-compliant sharing practices
- Use patient ID watermarks on medical records
- Set automatic expiration for patient documents
- Restrict access to authorized personnel only
- Maintain audit trails for regulatory compliance
Financial Services
- Apply regulatory compliance watermarks
- Use time-sensitive expiration for financial data
- Implement multi-factor authentication where possible
- Restrict access by IP address for internal documents
- Monitor for suspicious access patterns
Corporate Environments
- Use classification-based security levels
- Implement department-specific access controls
- Set business hours access restrictions
- Apply corporate branding to watermarks
- Integrate with existing security policies
Advanced Protection Strategies
Layered Security Approach
- Document Level: Watermarks and content protection
- Access Level: Email verification and view limits
- Network Level: IP restrictions and geographic controls
- Time Level: Expiration dates and access scheduling
- Monitoring Level: Real-time analytics and alerts
Risk Assessment Matrix
High Risk Documents:
- Legal contracts → Maximum security (1 view, 24-hour expiration)
- Financial data → High security (3 views, email verification)
- Medical records → Maximum security + audit trail
Medium Risk Documents:
- Business reports → Moderate security (10 views, watermark)
- Proposals → Standard security (unlimited views, expiration)
Low Risk Documents:
- Marketing materials → Basic security (watermark only)
- Public information → Minimal security (tracking only)
Common Security Mistakes to Avoid
Inadequate Access Controls
- Setting unlimited views for sensitive documents
- Using overly long expiration periods
- Failing to verify recipient identities
- Not monitoring document access patterns
Poor Communication Practices
- Sending secure links through unsecured channels
- Not providing clear access instructions
- Failing to notify recipients of expiration dates
- Not establishing document handling policies
Technical Oversights
- Forgetting to enable watermarks for confidential content
- Not testing security settings before distribution
- Failing to monitor analytics for suspicious activity
- Using generic security settings for all document types
Compliance and Legal Considerations
Regulatory Requirements
- GDPR compliance for European data subjects
- HIPAA compliance for healthcare information
- SOX compliance for financial reporting
- Industry-specific regulations and standards
Documentation and Audit Trails
- Maintain records of who accessed what documents
- Keep logs of security settings and changes
- Document sharing authorization processes
- Preserve access analytics for compliance reporting
Emergency Procedures
Breach Response Protocol
- Immediate Action: Revoke document access if possible
- Assessment: Determine scope and impact of exposure
- Notification: Alert relevant stakeholders and authorities
- Investigation: Analyze access logs and security settings
- Remediation: Implement additional controls and monitoring
Document Recall Process
- Monitor for unauthorized sharing or distribution
- Use analytics to track unusual access patterns
- Implement immediate access revocation when necessary
- Coordinate with recipients for secure document handling
Best Practices Summary
Before Sharing
- Classify document sensitivity level
- Configure appropriate security settings
- Verify recipient authorization
- Test access functionality
During Distribution
- Use secure communication channels
- Provide clear access instructions
- Monitor initial access attempts
- Be available for recipient support
After Sharing
- Monitor access analytics regularly
- Review security effectiveness
- Update settings as needed
- Maintain compliance documentation
Regular Security Reviews
- Audit document sharing practices monthly
- Update security policies based on threats
- Train staff on secure sharing procedures
- Test emergency response protocols
Remember: The goal is to balance security with usability. Over-restrictive settings can hinder legitimate business needs, while under-protection can expose sensitive information to unauthorized access. Find the right balance for your specific use case and industry requirements.